Zoom Security Features: Reduce the Odds of Zoombombing
Increase the security of your Zoom sessions to reduce the chance of unwanted attendees (“Zoombombing”). We recommend using as many of these options as you reasonably can without impacting your course or meeting.
This article applies to: Zoom
If you are discussing any sensitive or confidential information in your meetings, these measures become that much more important. If someone does sneak in, they could listen, capture screenshots, or disrupt the meeting with unwanted video or audio.
If someone you don’t know joins your meeting, instructions are available below to Remove a Participant. If one or more participants are being disruptive or abusive, consider the option to Suspend Participant Activities.
Update to the Latest Version
Always keep your Zoom client application updated to the latest version.
- For users with Cornell-managed devices, the latest version is available through Self Service for Macs and Software Center for Windows devices. Completing installation may require restarting your computer.
- Users with personally owned or non-managed computers should update Zoom by opening their profile settings (click your profile picture in the top-right corner), then clicking Check for Updates.
For full details, visit Check Your Zoom Application Version and Upgrade to the Most Recent Version.
Security Icon Options for Hosts
Zoom hosts will see the meeting Security icon. Clicking the icon shows a number of useful options in a single menu.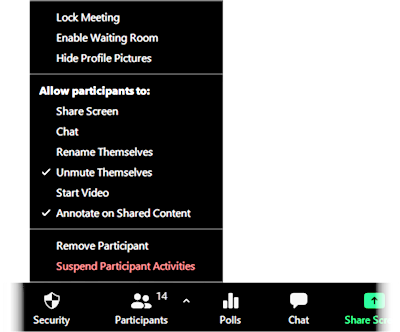
Hosts can toggle the following options on or off during meetings. Active features are identified with a checkmark. Clicking an active feature again toggles it off.
- Lock Meeting When a meeting is locked, no new participants can join—even if they are authorized users or have a passcode. See more below under “Lock Your Session.”
- Enable Waiting Room When this option is turned on, participants are placed in a virtual waiting room until admitted by the host. See more below under “Enable the Waiting Room.”
- Allow participants to:
Share Screen Turning this option off prevents participants other than the host from sharing their screens.
Chat Turning this option off prevents participants other than the host from using the Chat feature.
Rename Themselves Turning this option off prevents participants from renaming themselves in the meeting.
Unmute Themselves Turning this option off prevents participants from unmuting their audio without the host’s permission.
Start Video Turning this option off prevents participants from turning on their video without the host’s permission.
Annotate on Shared Content Turning this option off prevents participants other than the host from using annotation tools such as Draw, Stamp, Spotlight, Text, and Erase when screen sharing is used. This option is only visible to hosts when content is being shared.
- Remove Participant Dismiss a participant from the meeting. The removed individual cannot rejoin the meeting unless you have enabled Allow Participants and Panelists to rejoin in your Account Profile settings (link opens Zoom webpage).
- Suspend Participant Activities When turned on, this option stops all video, audio, in-meeting chat, annotation, screen sharing, and recording. A host could use this feature when an intruder disrupts a session, to block the ability of any participant to cause disruptions. Short of simply ending a session abruptly for all users, this option is a one-click solution for immediately stopping disruption or abuse by locking all participants’ features. For details about what happens when you use this option, see “Suspend Participant Activities,” below.
In addition to using the Security icon menu to control meetings, consider setting the following options when scheduling meetings:
Enable the “Waiting Room”
The Waiting Room feature lets hosts control when each participant joins the meeting. As the meeting host, you can admit attendees one by one, or hold all attendees in the virtual waiting room and admit them en masse. This requires more work by the host, but only allows participants to join if you specifically admit them.
Require User Authentication
Require attendees to authenticate by being signed in to Zoom using a Cornell NetID and password. Adding this measure can also save you from having to admit them from the Waiting Room, and also automatically provides their Cornell names in the meeting Participants list. See Require Authentication to Join Zoom Meetings for details.
Disable “Join Before Host”
If you are scheduling a meeting where sensitive information will be discussed, it’s best to leave Enable join before host turned off. (You can find the option under Meeting Options when scheduling a meeting.) Visit Zoom's Join Before Host help page for more information. It's strongly recommended that hosts also activate Only authenticated users can join when using this option.
The Join Before Host option can be convenient for allowing others to continue with a meeting if you are not available to start it, but with this option enabled, the first person who joins the meeting will automatically be made the host and will have full control over the meeting.
Another option is to assign an Alternative Host (opens page on Zoom website).
Meeting Passcodes
Meeting passcodes (previously called passwords) are now required. Passcodes are encrypted within the join meeting link and participants can join without entering it.
Attendees who only have the meeting number and not the full link that includes the passcode will need to enter this passcode to enter the meeting. You'll need to communicate your passcode to those attendees or use a passcode known by them already.
Limit Screen Sharing to the Host
By default, screen sharing in Zoom meetings is limited to the host. You can change this if necessary to allow other attendees to share their screens. If you do make this change and decide to return to having screen sharing be limited to the host, while in your meeting:
- Click the next to Share Screen.
- Select .
- Under Who can share, click .
This won’t be appropriate when multiple participants will need to share and collaborate, but this restriction prevents unwanted attendees from interrupting the meeting with intrusive sharing.
Meeting Security When Scheduling Zoom Meetings Using Your Outlook Calendar
If you add a Zoom meeting to your calendar using the Outlook Zoom add-in, the appointment text may include the full Zoom link including the encrypted Zoom meeting passcode. If you have set up your calendar so that it is open for all colleagues to view the details of your meetings, this can expose the ability to enter the meeting to anyone who views your calendar. You can protect the passcode by making the calendar entry private.
Remove a Participant from a Zoom Meeting or Webinar
If you have already begun a session and find an unwanted attendee has joined:
- If the Participants panel is not visible, click at the bottom of the Zoom window.
- Next to the person you want to remove, click .
- From the list that appears, click .
Suspend Participant Activities
What happens
When this option has been used to stop all video, audio, chat, screen sharing, annotation, and recording in a session, Zoom will prompt the host or co-host whether they would like to report a specific individual from the participant list, share details about the disruption, or include a screen capture of the disruption or abuse.
If the host chooses to report an abusive participant, that participant will be removed from the meeting, and Zoom’s Trust and Safety team will receive a notification of the incident. Zoom’s Trust and Safety team will send the host an email following the session to gather additional information.
Please report abuse during Cornell Zoom meetings to zoomsecurity@cornell.edu in addition to using the in-meeting Report option.
Resume the Interrupted Session
The host or co-cost can resume the meeting by going to the host menu Security icon and re-activating features listed in the Allow Participants to: section—for example, allow video, audio, chat, and sharing from participants once again.
Lock Your Session
The Security icon menu lets hosts quickly and easily lock a meeting by clicking Lock Meeting. Be aware that when a meeting is locked, no one else can join and you (the host or co-host) will NOT be alerted if anyone tries to join—so don't lock the meeting until everyone has joined.
If Zoombombing Abuse Does Occur
Be aware of the emotional impact that online abuse can have. Imagery that shows the violation of basic human rights (of adults or children) or targets a community is deeply troubling and can be traumatizing. Retraumatization of victims of sexual violence, assault, or discrimination is also possible. There is also a risk of inappropriate exposure to children who are in the home environment of the remote worker. If an event is intended for a child audience, consider recording the program instead of having it live.
If online abuse does occur (regardless of the audience), do not pretend that it did not happen and power through the meeting—and never just advise participants to simply look away. Rather, end the meeting swiftly and report the incident as soon as possible to Cornell Zoom Security at zoomsecurity@cornell.edu.
Then, follow up by email or other media to the participants to:
- apologize for the abrupt ending;
- indicate what steps are being taken to prevent reoccurrence;
- express care and concern for the participants; and
- offer available mental health resources.
Reporting Abuse
To report abuse directly to Zoom:
- Click Participants to show the list of meeting participants (if not already showing).
- Look for the name of the disruptive or abusive individual on the list.
- Click More beside the name of the disruptive individual.
- Then click Report.
Alternatively, hosts can report abuse by clicking the Meeting Information icon (green shield) at the upper left corner of the meeting window, then Report (red link with a flag icon).
Please report any incidents of abuse occurring in Cornell Zoom meetings to zoomsecurity@cornell.edu, in addition to using the in-meeting Report option.

Comments?
To share feedback about this page or request support, log in with your NetID