Protect Yourself Against a Two-Factor Phishing Attempt
Fraudulent emails (see how to spot them) are a common way to steal Cornell NetIDs and passwords, and gain access to your private information. Even with two-factor authentication enabled, criminals have found ways to trick users into giving away their login credentials.
This article applies to: Faculty , IT Professionals , National Cybersecurity Awareness Month , Security & Policy , Staff , Students , Two-Step Login
Beware of unexpected Duo (Two-Step Login) prompts. Ignore them unless you’re sure you requested them. If you are unexpectedly prompted to use Duo in a way you normally don’t, ignore it and contact the IT Security Office. For example, if you usually use your smartphone’s Duo app, but you instead get a Duo automated phone call or are prompted to enter a passcode, ignore it.
Be Wary of Repeated Login Attempts or Prompts
One way criminals try to get through your defenses is by chipping away at your patience. They start by stealing your NetID and password, then trying to log in to that account over and over and over and over... You get so many authentication requests on your phone that you might accidentally hit "accept" instead of "deny," or you might be tempted to turn off two-step authentication entirely.
The best way to stop this "MFA push spam" is to change your NetID password on the compromised account. Once you change your password, the attacker can no longer send you the authentication request. Contact the IT Security Office if this happens to you.
Look Out for Well-Done Fake Login Pages
Criminals may also trick you into giving them a legitimate two-factor verification code by lulling you into believing you're using a bona fide Cornell site. They send you an email that has a link going to a fake Cornell login page. Even though the page looks correct, the URL is the clue for you that something's not right. For links that take you to a login page, triple-check the webpage address in your browser bar.
The real CUWebLogin address starts with: shibidp.cit.cornell.edu/ (nothing between cornell.edu and the slash).
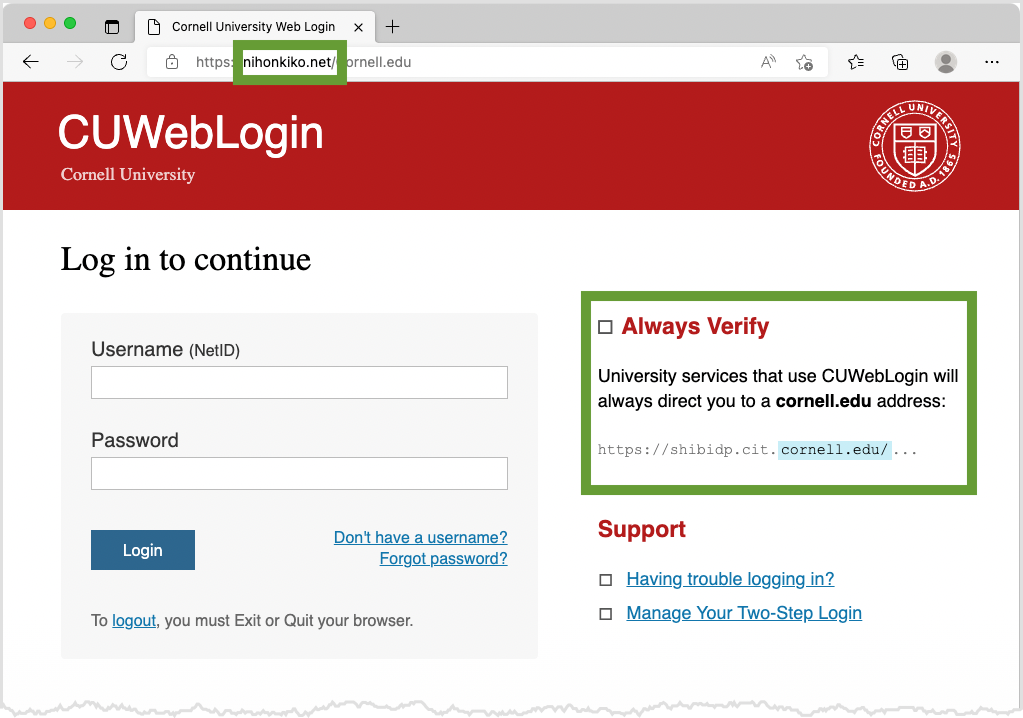
Once you enter your NetID and password on this fake page, you are asked to complete the two-factor authentication step. Normally Duo will use the method you used most recently, or the method you have chosen from the Other options list of methods.
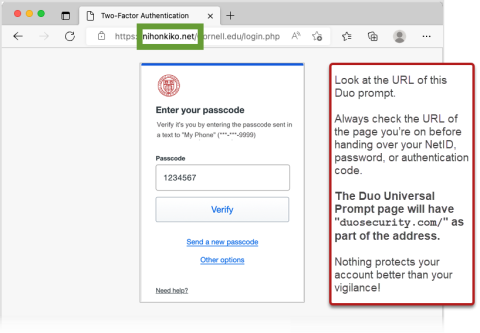
A phishing site will offer you ONLY the Enter a Passcode option, and will have an address from an unrecognized website domain.
duosecurity.com/ web domain.Graphically, everything looks legitimate, so you go to your phone, get the Duo passcode, enter it into the website, and click "Log in."
You’ve now been phished.
The criminal has:
- Your NetID
- Your password
- A legitimate Duo code that they can use to log in to your account
The strength of two-factor authentication lies in what you know (your login credentials) and what you have (your phone). If a website tries to bypass one or the other, then do not continue and contact the IT Security Office.
You’ll notice that this kind of attack originates with the link to the fake Cornell login page. That’s why it’s so important to make sure the link you click is a valid cornell.edu link. Remember, only the text between https:// and the next / tells the computer what server to use. https:/two-step lives on a Cornell server. https://it.scam.you/cornell.edu does not.
Report Suspicious Email with PhishAlarm
The button appears in different places, depending on your device and Gmail or Outlook interface. Examples and additional details can be found on the PhishAlarm instructions page.

Comments?
To share feedback about this page or request support, log in with your NetID