Latest News

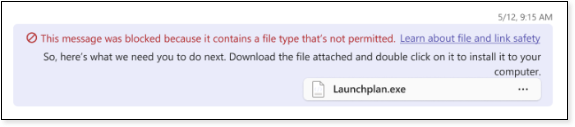
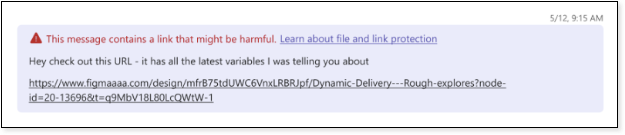
Starting in mid- to late November, Microsoft Teams will automatically block messages that include attached weaponizable files, and URLs that link to malicious sites. This applies to both internal and external Teams conversations.
File Blocking
When Microsoft detects a file upload that contains one of the extensions listed below, it will block the file completely and display a warning message to the sender.
File types affected by this change include the following extensions
ace, ani, apk, app, appx, arj, bat, cab, cmd, com, deb, dex, dll, docm, elf, exe, hta, img, iso, jar, jnlp, kext, lha, lib, library, lnk, lzh, macho, msc, msi, msix, msp, mst, pif, ppa, ppam, reg, rev, scf, scr, sct, sys, uif, vb, vbe, vbs, vxd, wsc, wsf, wsh, xll, xz, z
How to Share Safe Files
If you need to send a file with this file type, and you are certain that it is a safe file, share the file via Box, SharePoint, OneDrive, or Secure File Transfer as appropriate.
Link Blocking
Similar to Safe Links, if someone shares a link to a potentially dangerous site, Teams will automatically block the link and display a warning.

Comments?
To share feedback about this page or request support, log in with your NetID