Changes to Authentication Process for Microsoft Admin Portals
This article applies to: Authentication
CIT is implementing the following features for authentication to Microsoft Admin Portals, including Azure, Entra, Intune, and M365:
- New Multifactor Authentication (MFA) with Duo to comply with Microsoft’s mandatory MFA requirements
- A 10-hour token session limit
New Multifactor Authentication
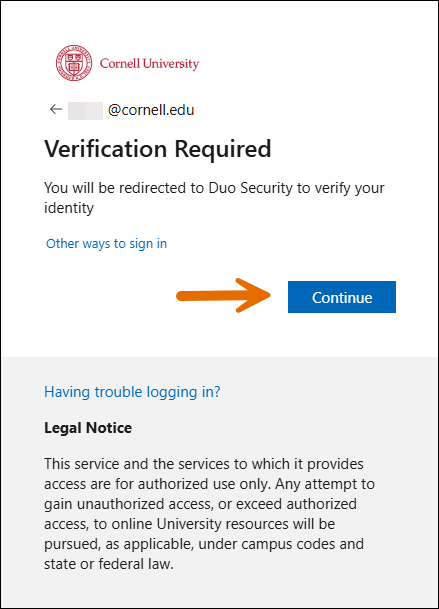
Microsoft now requires MFA for their admin portals. You will receive an additional prompt during login as outlined below:
- Open the admin portal logon page.
- Enter your admin username.
- Enter your password. A Verification Required window will display.
- Click .
- Verify with Duo.
Submit a ticket to the IT Service Desk if you experience any issues with the verification process.
10-hour Session Limit
An authentication token’s lifetime is now limited to 10 hours. This means you will be prompted to re-authenticate after 10 hours from when you initially logged in. This is not an inactivity timeout – the timeout can occur even when you are actively working in a portal.
Troubleshooting
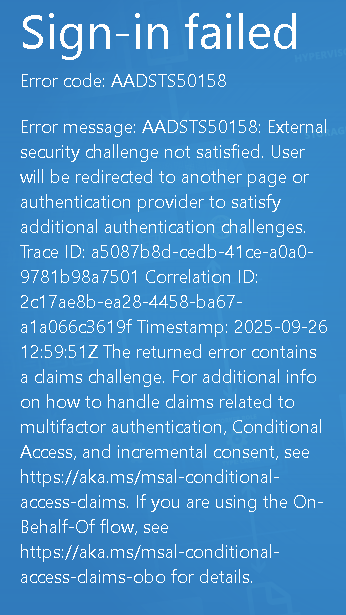
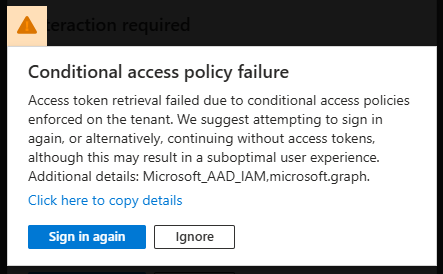
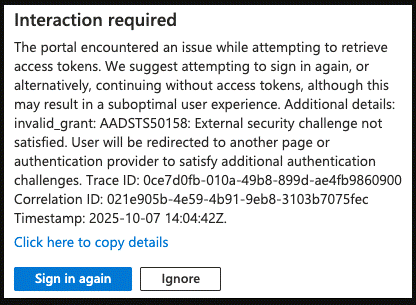
If you receive one of the errors below, or an error that's similar, try the following options:
- If available, click the button. Several attempts may be necessary to succeed.
- If no button is available, please wait 15 minutes before attempting to log in again.

Comments?
To share feedback about this page or request support, log in with your NetID