Identify Risky End-user License Agreements (EULAs)
How to spot red flags in End-User License Agreements
This article applies to: Security & Policy
When you’re online, be particularly wary if you are asked to install software—even if it appears fairly harmless.
Before downloading and installing any new software, always read the EULA, the legal statement that you agree to before you can install the software.
Try to assess the Intentions of the Software Provider
- Generally, references to market research in a EULA are a red flag.
- The fine print in the EULA might grant fairly broad access to your computer and your activities, with surprising latitude in what can be done with the information collected.
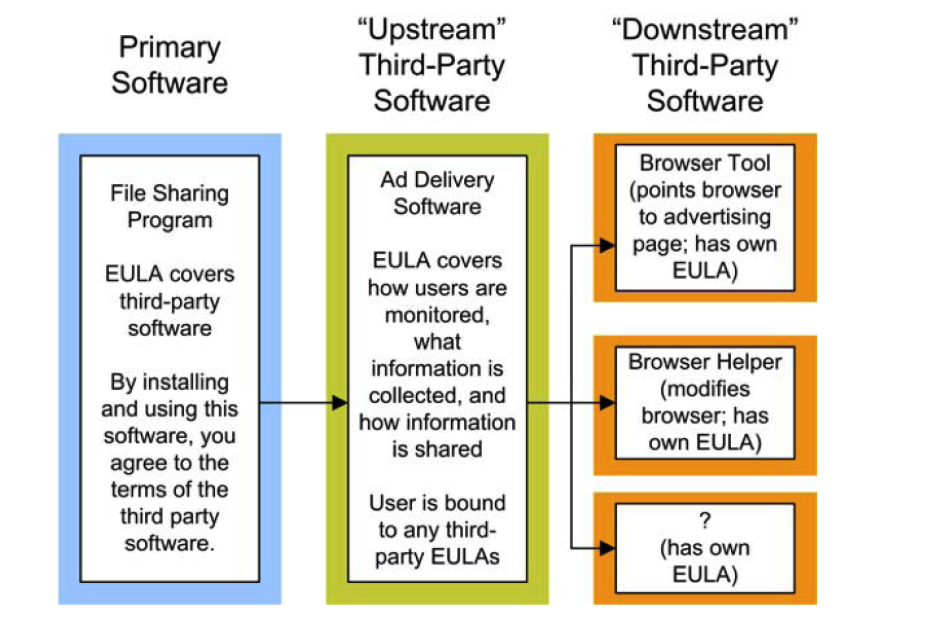
- Cascading EULAs are a particular concern. These include EULAs that grant access to a third-party, which in turn can grant access to another third-party, and so on, thereby legally granting access to your computer for multiple unknown parties.
The following diagram, provided by the US Computer Emergency Readiness Team (www.us-cert.gov), illustrates the problem with cascading EULAs:
For a list of what you can do to protect yourself, download Software License Agreements: Ignore at Your Own Risk, a PDF.

Comments?
To share feedback about this page or request support, log in with your NetID